Is Hardware Technology Important for Cybersecurity?
Cybersecurity is becoming very popular, as both industries and individuals are interested in data security. Technology is blooming rapidly, but unfortunately, with its advancements, people’s privacy has become more vulnerable. Every day, we hear about cases of data piracy, identity theft, and blackmail. Industries also face threats to the security of their data, putting sensitive information at risk.
The most burning question Is Hardware Technology Important for Cybersecurity. Data safety is crucial. To ensure it, software has been created. Without hardware, software is nothing, and without software, hardware has no use. Both need to work together and be matched according to their capacity. Cybersecurity is a wide field that ensures everything specified for improving security, such as developing protective software, developing the right hardware, building safe networks, and maintaining security systems.
The goal of hardware technology in cybersecurity is to keep hardware devices safe. Its main purpose is to sketch strategies to protect hardware from malicious activities.
The technology focuses on hardware’s integrity, solitude, and availability of hardware devices and the data it will process. Risk management proposed by this technology is responsible for pointing out threats that any hardware asset faces, like malicious activity, whether connected by USB or network interfaces.
Hardware and Software Protection in Cybersecurity
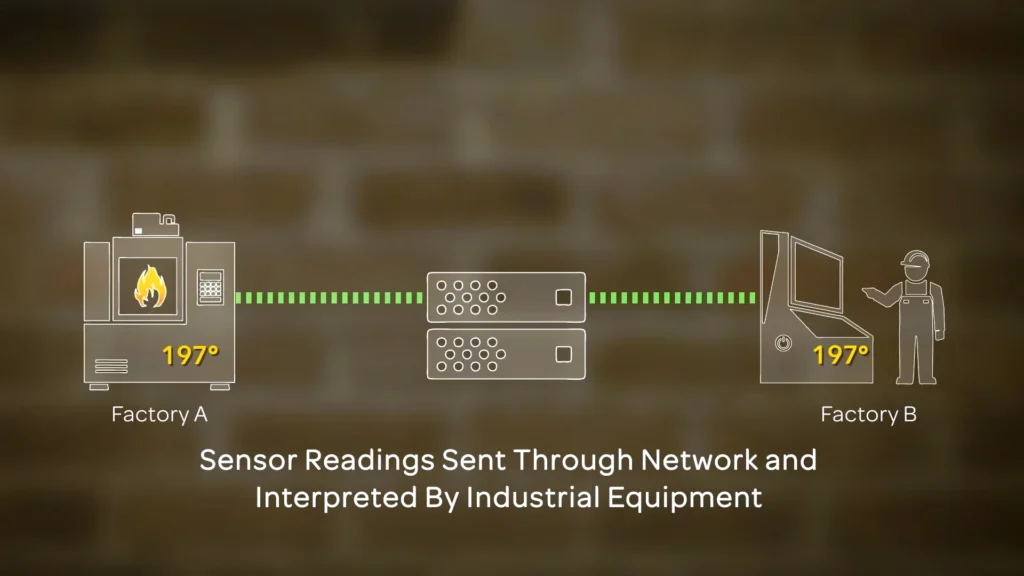
Hardware security and software protection are both important for cybersecurity. Hardware technology provides physical protection. Some applications, like firewalls and encryption tools, are used in this regard; they have inbuilt features that can stop threats and scams from entering our system. If we accidentally install malicious software on our device, this protective security software can detect and stop that digital attack.
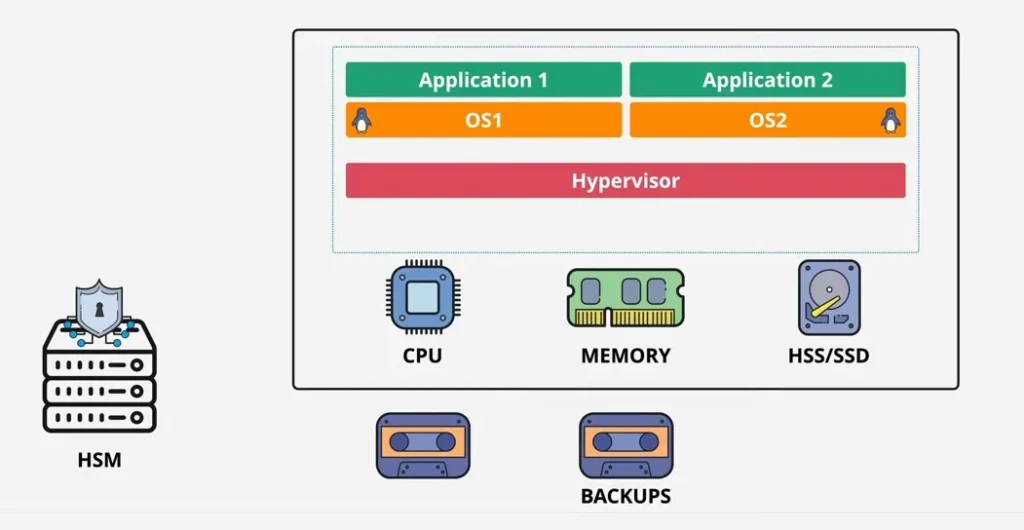
This combination of software and hardware provides a strong, opposing wall resistant to cyber threats. Hardware provides security from external hazards, and software provides security from risks expected inside the system. They protect private information and maintain uninterrupted system functionality when used in tandem.
Hardware and Software Security
Cybersecurity has two fundamental layers: hardware and software. Each layer helps to protect the systems against threats.
Hardware security

To protect physical parts such as processors, microchips, and circuit boards from tempering, unauthorized modifications, and hardware-based attacks. For instance Trusted Platform Modules (TPMs) and Hardware Security Modules (HSMs).
Software security
Programs and protocols are used to defend against digital threats like malware, phishing, and unauthorized data access, such as Firewalls, encryption software, and antivirus programs.
Key Differences and Collaboration
Hardware security protects the physical components, while software security protects the programs, applications, and data. Hardware and software are important for a comprehensive protection strategy. Hardware protects the foundation, and software provides real-time protection.
The Importance of Cybersecurity Hardware and Software
Cybersecurity concerns protecting data and systems from digital scams. Hardware and software are both important and work together, they work to fulfill the purpose of cybersecurity.
Protecting Sensitive Data
Hardware technology offers secure storage to keep data safe from malware. Hardware security devices like trusted platform modules (TPM) are used to save encryption keys and other sensitive information even during violation. Encryption helps to keep data secure and unreadable even if hackers somehow access it. Some modern devices have a built-in TPM feature to secure sensitive data.
Sensitive data includes private information, passwords, and financial information. To avoid theft, we should take preventive measures, such as changing passwords often and using two-factor authentication.
Preventing Cyber Attacks
Hardware technology is responsible for developing encrypted tools, such as USB sticks, which have special chips that can automatically encrypt information. These add an extra layer of security over software measures, so hackers can’t read encrypted data easily.
Hackers always look for gaps in the system. To avoid digital attacks, try to block traffic that would harm our systems. Install updated and strong firewalls in the system. Also, install antivirus software to protect and detect any malicious activity.
To avoid unwanted activity, try to follow measures like updating software regularly, training for cybersecurity practices, using solid passwords, and continuously monitoring your system.
Ensuring Seamless Functioning
Ensure all the tools, hardware, and software work properly and correspondingly to protect your system. The hardware must be properly set up. Besides this, try to update the hardware setup regularly. Learn every step of the information flow so that you may find out the cause of the problem at any stage. Make sure everything is getting done properly.
Device Authentication And Integrity
As software prevents digital attacks, there is an additional threat of physical attack. For this purpose, physical authentication devices like thumbprint detectors, fingerprint detectors, card authentication, and retina detectors are introduced. These devices need the physical presence of an object trying to reach information or data. This audacity is added to the layer of security measures.
Preventing Rootkits Attacks
Criminals are strengthening their techniques and expertise daily. They try to break the firmware and corresponding hardware of the system. With the help of a rootkit, they occupy the system’s main control or administration and hide it in the system’s roots. It is difficult to find such fraudulent activity even with antivirus or detective software.
However, modern development systems, such as Intel’s Trusted Execution Technology (TXT) and AMD’s Secure Processor (SP), can detect these types of attacks and ensure firmware integrity.
Is hardware technology important for cybersecurity?
Hardware security plays an important role in establishing a foundation for digital systems. Software security helps to protect applications, programs, and data, while hardware protects the physical layer.
Key Benefits of Hardware Security
Physical Protection
Hardware security provides complete protection for physical components and reduces the risk of unauthorized access.
Tamper Resistance
The tamper-proof module detects the response to the physical attempts to alter a device.
Isolation from Software Vulnerabilities
Hardware security helps to operate independently.
Key Examples of Cybersecurity Hardware
Trusted Platform Module (TPM)
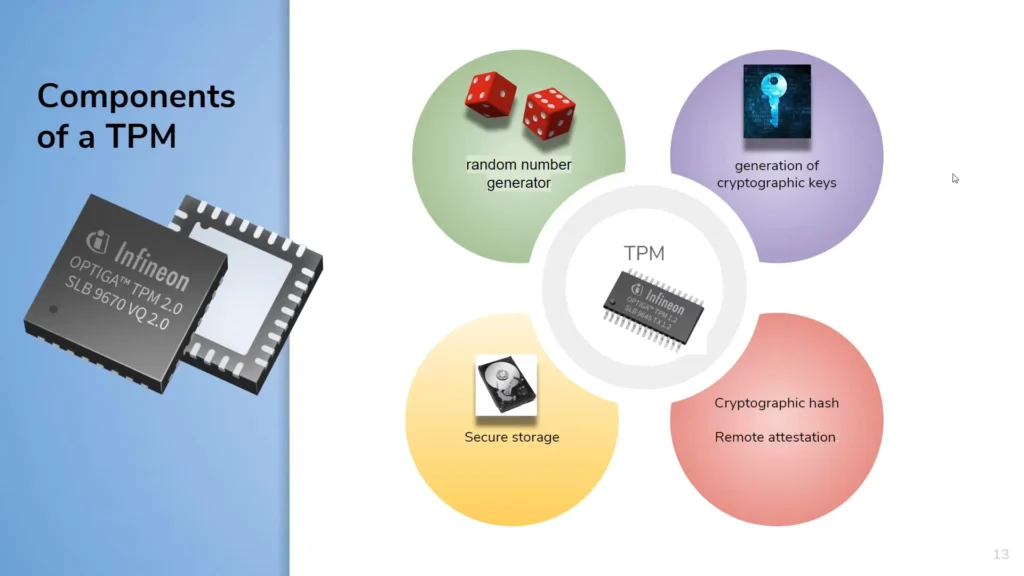
A trusted platform Module is a microcontroller computer chip that can be used to save artifacts and authenticate your PC or laptop. Is Hardware Technology Important for Cybersecurity?
Secure Boot Mechanism
Is Hardware Technology Important for Cybersecurity? A secure boot mechanism verifies the system’s authenticity and ensures that no unauthorized data access occurs.
Data Diodes

Is Hardware Technology Important for Cybersecurity? A security product accesses a critical system to prevent data from external threats. It has two nodes: one sends data, and the other receives data.
Tamper-Proof Modules
Is Hardware Technology Important for Cybersecurity? Tamper-proof modules are physical devices and infrastructure that protect content from unauthorized access.
Why Hardware Security Matters?
Hardware cybersecurity is often less important than network and endpoint security. But we cannot deny its influential value because it protects physical components from attacks. Is Hardware Technology Important for Cybersecurity?
Attacking devices mostly successfully hide themselves
They manage to escape from radar, the human eye, and even detection software. These devices are generally called rogue devices. Existing cybersecurity tools are also unable to detect them.
This false sense of guarding leads to great damage to sensitive data or information when network enterprises face potential data breaches. Strong hardware devices equipped with the latest technology must be integrated into the system to stop hardware attacks from rogue devices.
Hardware Cyber Security Risk Awareness
Is Hardware Technology Important for Cybersecurity? Employees of the organization or industry and all stakeholders associated with any firm continuously get training to save their assets from suspicious attacks. They are guided to detect malicious USB drives or links supported by malware attacks.
So that they do not need to connect USB sticks or click any suspicious link that may cause damage to their privacy after entering into their system silently; after security training, employees can protect their assets. They can help prevent their organization’s assets from being compromised.
Although organizations enhance their security against cyberattacks, hardware technology is still partially neglected, hence leaving assets exposed to cyberattacks. So typical security measures such as Network Access Control (NAC), Intrusion Detection Systems (IDS), and IoT network security cannot detect rogue devices such as USB HID-emulating devices or physical layer network insertion. In this way, hackers can enter our system administration without detection and make changes according to their will.
Prioritize and Mitigate Hardware Asset Risks
To develop a strategy for hardware technology, comprehensive knowledge about the inner system and assets is necessary. But the game-changing technique is how you use this information practically.
After a complete go-through, you can clearly identify which device needs more attention for security purposes in the network. We get alerts for high, medium, and low risks after using DNA technology and policy rules. Is Hardware Technology Important for Cybersecurity? Reforms like
- Speeding up the resolution process
- Highlighting regulatory gaps
- And stopping hardware-based attacks.
With real-time visibility, your security team can better understand the risks to your devices and take action to secure them. Preventing social engineering attacks and denial-of-service attempts is key to securing your company’s infrastructure.
Improve Your Cyber Security Posture
An assessment provides a comprehensive view of your company’s hardware security. Identify flaws, make wise improvements, and improve your overall security. Discover the strength and valuable risk information it provides for improving network hardware security. Speak with an expert to understand how to leverage proprietary technology to manage your asset risks.
Cybercrimes Involving Hardware Attacks
There is a big difference in the composition of malicious software and hardware. Malicious software can be developed by any individual and deployed anytime using software or internet traffic. But the case is different on the hardware side. Malicious hardware can only be produced in the form of chips at the time of manufacturing. Only the person with access to the manufacturing process and the knowledge to make and alter the chip can do so.
Introducing harmful changes during manufacturing is frequently ineffective, as these changes exhaust the chip to the point where it fails quality tests. This is because most harmful modifications occur during the design process when specific functions of the chip are mapped out. Malicious hardware may not be used to initiate an attack for months or even years after deployment.
Attacks can occur in a variety of ways. Particular things, such as a date or a specific place, like a GPS point, set some off. When an attacker is prepared to launch an attack, they can also conceal and activate a trigger inside external data.
Overt assaults can cause a device or system to operate impaired or to fail and shut down. These attacks are designed to silently corrupt data and do malicious activities in the background while showing that the device or system works normally. Covert assaults could potentially open the door to allow the distribution of harmful software at a later point.
Importance of Hardware-based Cybersecurity
In this era where every field is unquiet with digital maps, depending on hardware-based security is not just an option; it’s necessary to keep data protected. It is a barrier that secures our digital assets from cyberattack threats and risks.
Is Hardware Technology Important for Cybersecurity? According to a recent study, 63% of firms had at least one data breach due to hardware security flaws in the preceding year. This distressing number underlines the need for hardware-based cybersecurity to protect digital assets and maintain system integrity.
Furthermore, hardware-based cybersecurity is more important than just protecting data. It is key to ensure that digital systems are well-grounded and always available. Lack of strong hardware security may make systems receptive to interruptions, which might have serious operational and financial significance.
Advantages
Although software security measures have their advantages, we cannot deny the importance of hardware security. Is Hardware Technology Important for Cybersecurity? Some advantages are as follows:
- As it is tangible, it can be physically protected because it’s a piece of hardware.
- In comparison to software, hardware solutions frequently complete tasks more quickly.
- Hardware components are naturally immune to vulnerabilities and gaps in software.
- Hardware solutions require fewer upgrades or adjustments and often survive longer.
Hardware Cybersecurity Applications in the Industries
Is Hardware Technology Important for Cybersecurity? The world is fast moving towards digital processes, and different industries tend to rush towards hardware cybersecurity to keep their operations and assets safe from risks and threats.
Here are some hardware-specific cybersecurity examples
- Energy and Utilities
- Unidirectional Gateways: It permit data to move out of a secure network system but do not let harmful data reenter the system. This technique is crucial for power plants and substations.
- Firewalls: Preventing unwanted access, especially in nuclear and hydroelectric plants. In this scope, malicious activity can cause a big disaster.
- Secure Servers: Energy grid infrastructure is important for running a state. Hardware security applications protect energy grids and their operational data and safeguard their infrastructure.
- Manufacturing
- Intrusion Detection Systems: This system monitors machinery and production and ensures proper working of operations.
- Tamper-proof Modules: These modules defend the integrity of machinery. They ensure that production quality is up to the mark; there is no compromise over quality.
- Industrial Control System (ICS) Protectors: This system is specifically designed to protect the structures that run heavy machinery.
- Mining and Metals
- Unidirectional Gateways: These gateways transfer data from archaeological sites without risk.
- Tamper-proof Modules: Protect appliances in remote areas from physical damage.
- Intrusion Detection Systems: Protect mining workers and mining operations from expected threats.
- Oil and Gas
- Firewalls: Safeguard critical operational data, like drilling locations and extraction processes.
- Intrusion Detection Systems: Look for expected threats in offshore rigs and pipelines.
- Secure Routers: Is Hardware Technology Important for Cybersecurity? In areas of political sensitivity, secure communication between exploration sites and the main office is ensured.
- Chemicals and Pharmaceuticals
- Firewalls: Safeguarding chemical formulas and medicine recipes for pharmaceutical companies.
- Tamper-proof Modules: Keep product quality unscratched. Make sure the equipment used in the production of drugs is secure.
- Intrusion Detection Systems: Monitoring for irregularities in production where even small deviations can result in major effects.
Hardware Cybersecurity Examples in Real-World Applications
Is hardware technology important for cybersecurity in critical industries? Yes, hardware cybersecurity is important in critical industries where data is paramount.
Critical Infrastructure Protection
Is Hardware Technology Important for Cybersecurity? Cybersecurity is a process used to protect systems and assets from threats like cyber attacks, natural disasters, and terrorism.
Power Grids & Substations
Is Hardware Technology Important for Cybersecurity? Data does, and secure routers are used to secure the unidirectional flow of data and secure remote access threats.
Nuclear Facilities
Various systems are used to protect systems from unauthorized physical and digital access. For instance, tamper-proof modules and intrusion detection system.
Medical Devices
Pacemakers and image machines secure the boot mechanism from tempering during operation.
Patient Data Protection
Hardware encryption modules protect sensitive patient data during transmission and storage.
Financial Institutions
ATMs and POS Devices
Is Hardware Technology Important for Cybersecurity? Hardware security modules are used to protect data from interception and alteration.
Data Centers
Physical access controls are used to protect data centers from unauthorized access. Is Hardware Technology Important for Cybersecurity?
Government and Defense Systems
Secure Communications Equipment
Communication of the defense system is secured with encryption with hardware modules.
Surveillance Systems
Surveillance systems are used to protect data from manipulation.
How Software and Hardware Work Together in Cybersecurity
Hardware security protects the foundation layer, while software security protects the digital system. A multi-layer defense strategy protects against diverse cyber threats.
The Role of Software in Cybersecurity
Cybersecurity detects, mitigates, and responds to software-based threats like unauthorized access, malware, and ransomware. Various software, such as antivirus software, firewalls, and intrusion detection systems, are used to protect against cyber threats.
How Hardware Complements Software Security
Physical security
Hardware security protects against various threats, such as hardware Trojans and tempering at the manufacturing level.
Root of Trust
Level of trust in software that is running a system.
Cryptographic Protection
TPMs and HSMs are hardware modules that store and safeguard data and encryption keys.
Challenges and Risks of Inadequate Hardware Security
Inadequate hardware security can create significant vulnerabilities. These risks can seriously affect critical sectors such as finance, health care, and defense.
Supply Chain Vulnerabilities
Globalization helps to outsource production in semiconductor manufacturing. Compromised chips can create serious concerns. Malicious circuits embedded within the chips during fabrication also create vulnerabilities.
Hardware Backdoors and Trojans
Malicious circuits embedded within the chips help create covert backdoors, which allow attackers to bypass security protocols. It is difficult to detect these threats unless a significant breach occurs.
Lack of Secure Manufacturing Standards
Many manufacturers lack robust security measures during the production phases. Compromised components can be integrated into the critical system.
Consequences of Hardware Vulnerabilities
Is Hardware Technology Important for Cybersecurity? Compromised hardware can expose sensitive information.
Trends and Innovations in Hardware Security
Is Hardware Technology Important for Cybersecurity? Cybersecurity has introduced innovative advancements in hardware security to counter threats. These innovations help protect both physical and digital systems from cyber attacks.
Zero Trust Hardware Architecture
Is Hardware Technology Important for Cybersecurity? The zero-trust model is famous in network security, but it is also famous in hardware security. It is important to verify each part of the hardware before it functions.
AI-Enhanced Threat Detection
Integrating artificial intelligence with hardware technology is used to detect anomalies in the physical layer.
Conclusion
Is hardware technology important for cyber security? Hardware technology plays a vital role in cybersecurity by providing an additional protection layer over software-based solutions. While software security provides protection against evolving digital threats, hardware security helps to form a resilient defense strategy.
Frequently asked questions
Q 1. What is the importance of hardware technology?
Ans. Hardware technology is important to ensure the reliability, integrity, security of digital system. It can be used to provide fundamental elements such as copy right modules, tamper proof designs, secure storage, and software solutions.
Q 2. What kind of technology is needed for cybersecurity?
Ans. A combination of both software and hardware strategy is required for cybersecurity. Firewalls, intrusion detection system, hardware security modules, and biometric authentication are essential hardwares for cybersecurity.
Q 3. What is the most important tool in cybersecurity?
Ans. Integration tool that is used to integrate the software and hardware. Secure tokens and TPMs are essentials for authentication and encryption.







